Conclusion
After conducting
this forensic analysis of the IDrive Windows application, the investigator
found that the data is stored in two default locations, which are: “C:\Program Files (x86)\IDriveWindows\”
and “C:\Users\username\AppData\Local\IDrive\”. Within this second location most of the
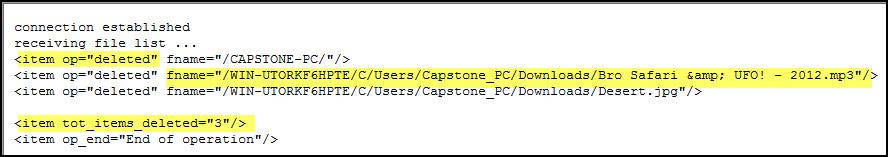
important forensic artifacts are stored, including logs, which provide details
about every action performed within IDrive and every file that was ever backed
up, restored, deleted, cleaned up, and moved from the IDrive trash to the
original location within the IDrive backup set.
Also, when a
file is deleted within the IDrive backup set, it is moved to the IDrive trash,
which is recorded in a log. These files
still remain on the computer however.
Once the files are deleted from the IDrive trash, the files still remain
on the computer, but they don’t remain in the IDrive backup set until they are
backed up again. This data is again,
recorded in a log. Once a backed up file
is deleted from the computer itself, the user can run Archive Cleanup, which
removes it completely from the IDrive backup, which is logged as well.
It was also
found that an investigator can find the computer name and the IDrive username
from the artifacts generated by IDrive.
The investigator was able to prove that it is possible to recover the
username and password of the IDrive account by acquiring and analyzing a RAM
dump of the computer.
An investigator
will additionally be able to tell if another computer was backed up to IDrive
using the same IDrive account, as the computer name for each connected computer
is used as the parent folder in the backup set to store the data. An investigator will be able to tell if
another drive was connected to a computer, if the contents of this drive were
backed up to IDrive, as there is a drive letter associated with the drive and
shown in the IDrive backup set.
Furthermore, if
a user shares files from IDrive via Twitter or Facebook, the investigator will
have the ability to find the files that were shared. He or she will be able to have access to the
URL that is generated from IDrive, which is used to share the files.
Moreover, the
investigator found 4 files are generated on the computer during install of
IDrive, which connect to the Internet to send data and reach out to the IDrive
website, as well as IDrive’s host company.
These files used various protocols and ports to connect out to the
Internet.
Once IDrive is
unistalled, an investigator will still have access to all of the important
artifacts, as the AppData Local IDrive folder is not deleted after
uninstall. This will allow an
investigator to conduct a thorough investigation even after a user attempts to
remove evidence of the IDrive Windows application. Everything that a user does
within IDrive, can be found out by an investigator because everything is
documented by logs and session files.